Single Sign-On Overview
Pipedream supports Single Sign-On (SSO) with Okta, Google, or any provider that supports SAML or Google OAuth, which allows IT and workspace administrators easier controls to manage access and security.
Using SSO with your Identity Provider (IdP) centralizes user login management and provides a single point of control for IT teams and employees.
Requirements for SSO
- Your workspace must be on a Business or Enterprise plan
- If using SAML, your Identity Provider must support SAML 2.0
- Only workspace admins and owners can configure SSO
- Your workspace admin or owner must verify ownership of the SSO email domain
The below content is for workspace admins and owners. Only workspace admins and owners have access to add verified domains, set up SSO, and configure workspace login methods.
Verifying your Email Domain
In order to configure SAML SSO for your workspace, you first need to verify ownership of the email domain. If configuring Google OAuth (not SAML), you can skip this section.
- Navigate to the Verified Domains section of your workspace settings
- Enter the domain you'd like to use for SSO (for example,
example.com), then click Add Domain - You'll see a modal with instructions for adding a
TXTrecord in the DNS configuration for your domain - DNS changes may take between a few minutes and up to 72 hours to propagate. Once they're live, click the Verify button for the domain you've entered.
- Once Pipedream verifies the
TXTrecord, we'll show a green checkmark on the domain
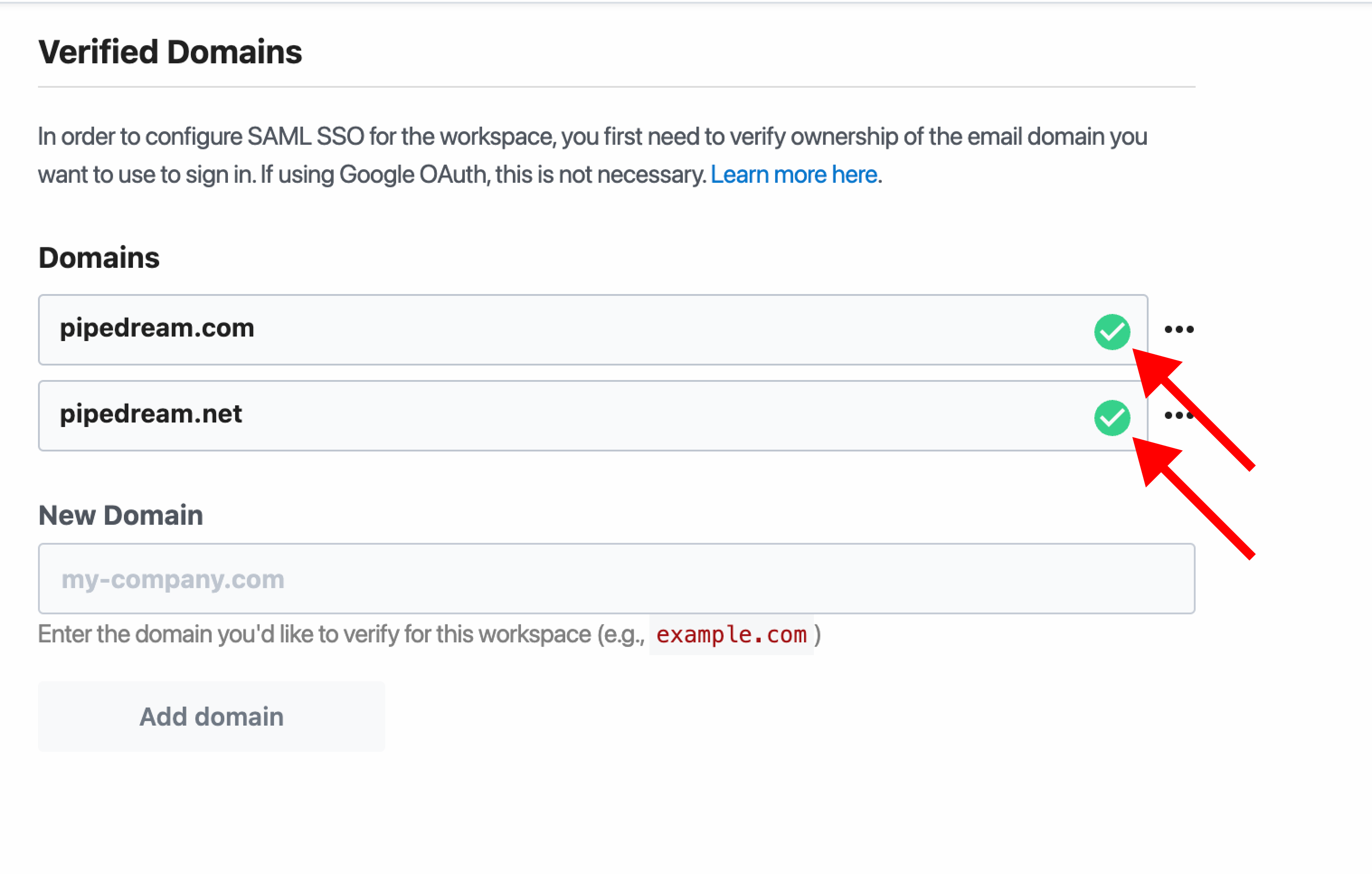
Make sure to verify all your domains. There's no limit on the number of domains you can verify for SSO, so if you use example.com, example.net, and foo.example.com, make sure to verify each one.
Setting up SSO
Navigate to the Authentication section in your workspace settings to get started.
SAML SSO
- First, make sure you've verified the domain(s) you intend to use for SSO (see above)
- Click the Enable SSO toggle and select SAML
- If setting up SAML SSO, you'll need to enter a metadata URL, which contains all the necessary configuration for Pipedream. Refer to the provider-specific docs for the detailed walk-through (Okta, Google Workspace, any other SAML provider).
- Click Save
Google OAuth
- Click the Enable SSO toggle and select Google
- Enter the domain that you use with Google OAuth. For example,
vandalayindustries.com - Click Save
Restricting Login Methods
Once you've configured SSO for your workspace, you can restrict the allowed login methods for non-workspace owners.
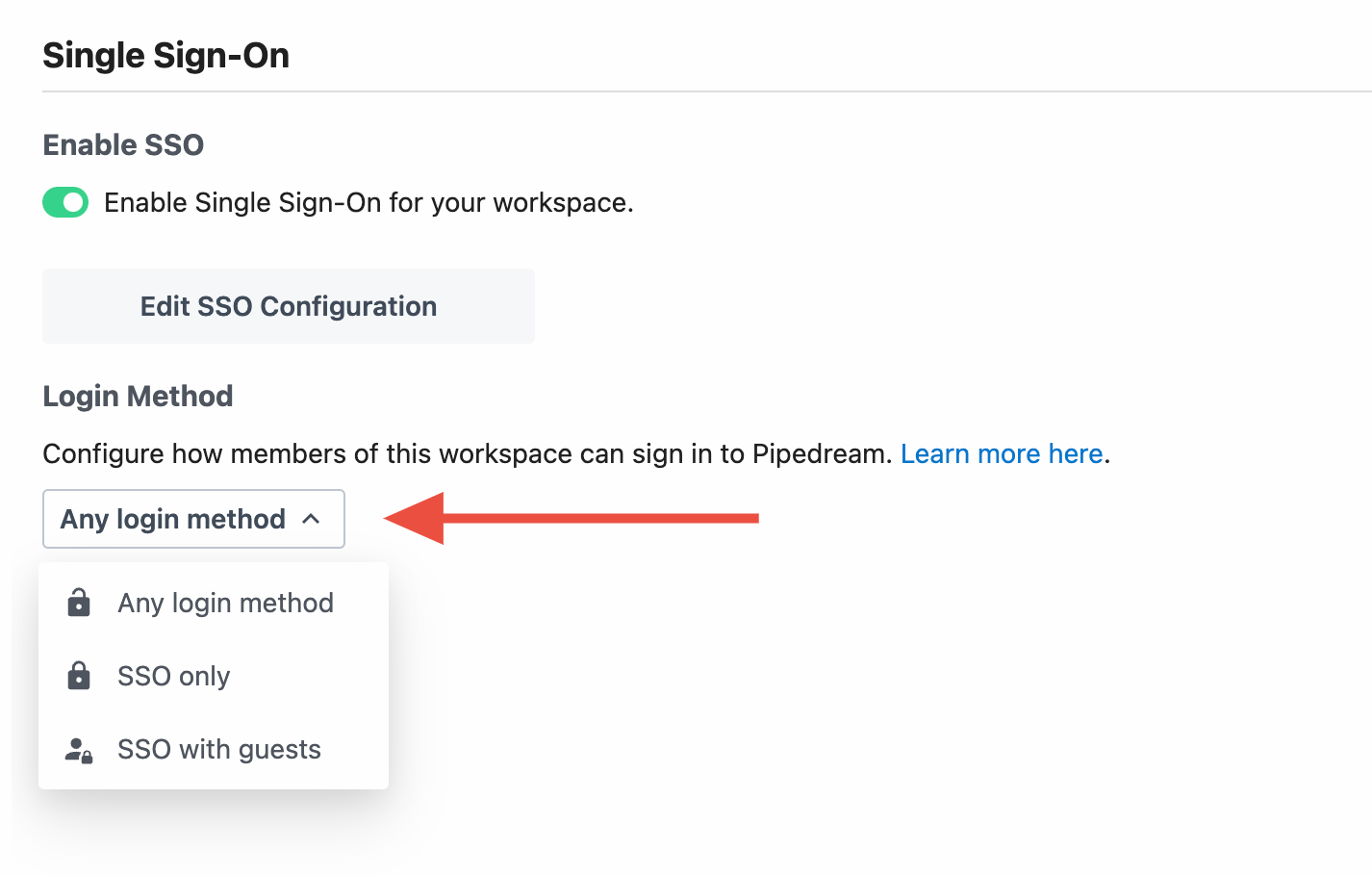
| Login Method | Description |
|---|---|
| Any login method | Everyone in the workspace can sign in either using SSO or via the login method they used to create their account (email and password, Google OAuth, GitHub) |
| SSO only | Workspace members and admins must sign in using SSO |
| SSO with guests | When siging in using a verified email domain, members and admins must sign in using SSO. If signing in with a different domain (gmail.com for example), members (guests) can sign in using any login method. |
Workspace owners can always sign in using any login method
In order to ensure you don't get locked out of your Pipedream workspace in the event of an outage with your identity provider, workspace owners can always sign in via the login method they used to create the account (email and password, Google, or GitHub).
Login methods are enforced when signing in to pipedream.com
This means if you are a member of 2 workspaces and one of them allows any login method but the other requires SSO, you will be required to sign in to Pipedream using SSO every time, independent of the workspace you are trying to access.